How I bypassed the otp verification Hack 100% Working
After reading this I realised that I have had always tried different ways to try and bypass the login credentials but never those which had OTP verification process. So this article gave a me this feel that online profiles which have inbuilt OTP verification process is not super secure as well and from there onward I tried to carry out some attack on a website that uses OTP verification process.
Let’s dig in! I started my attack on this website let’s say example.com, here I carried out my attack in two phase. Can I create a profile using a mobile no. that I don’t own? ( Identity theft ) Can I get access to the account of a person, if all I know is their username or mobile number? ( How I bypassed the OTP verification process? Part — 2 )
The First Hack
So to understand how to create a profile and how the system of OTP works on that particular website I went ahead and created my account. While I was doing that I took notice as to how the website worked?. Once done then I carried it out again for the another number that I own but this time the whole Idea was to create the account without having to touch my phone in anyway in which the sim was inserted. So, here is how I began doing the hack. I inserted all the details as it should be. Now as I was done with it, I received an OTP on my phone instantly to verify and complete the process of a creating the account.
Burp Suite On !
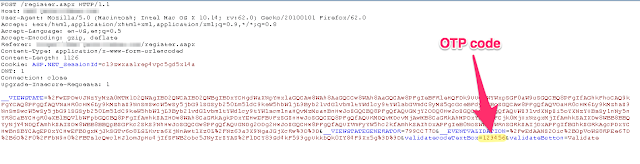
I was presented with this and had to put in the OTP that I had just received on my mobile. I turned intercept mode on, and captured the packet which was being sent over as a request packet to the server.
I already knew the OTP is a 6 digit number, as I received so when I made my first account. So, I passed over the packet to the intruder tab to carry out a brute force attack and see if the website allowed multiple attempts for the OTP. Now, to figure it out I carried out a brute force attack, for the first attempt I saw the OTP that I got and made a long list of nearly 150 number and included it at the very end to just know if the process will work out or not.
I guess I was in luck when the brute attack worked. Burp Suite was able to detect which one was the correct OTP. Moral This is one of the biggest mistakes that i have encountered in my time while carrying out pen-testing, where we never check the number of times the OTP is entered, or the number of times passwords are entered etc. Prevention method for such brute force attacks could be a check that disallows any attempt made more than 3–5 times, or the OTP should not be valid further after 5 wrong attempts or so. This kind of security technique can be implemented and it will help curb a huge number of security issues. If you enjoyed it please do clap & let’s collaborate. Get, Set, Hack!
After reading this I realised that I have had always tried different ways to try and bypass the login credentials but never those which had OTP verification process. So this article gave a me this feel that online profiles which have inbuilt OTP verification process is not super secure as well and from there onward I tried to carry out some attack on a website that uses OTP verification process.
Let’s dig in! I started my attack on this website let’s say example.com, here I carried out my attack in two phase. Can I create a profile using a mobile no. that I don’t own? ( Identity theft ) Can I get access to the account of a person, if all I know is their username or mobile number? ( How I bypassed the OTP verification process? Part — 2 )
The First Hack
So to understand how to create a profile and how the system of OTP works on that particular website I went ahead and created my account. While I was doing that I took notice as to how the website worked?. Once done then I carried it out again for the another number that I own but this time the whole Idea was to create the account without having to touch my phone in anyway in which the sim was inserted. So, here is how I began doing the hack. I inserted all the details as it should be. Now as I was done with it, I received an OTP on my phone instantly to verify and complete the process of a creating the account.
Burp Suite On !
I was presented with this and had to put in the OTP that I had just received on my mobile. I turned intercept mode on, and captured the packet which was being sent over as a request packet to the server.
I already knew the OTP is a 6 digit number, as I received so when I made my first account. So, I passed over the packet to the intruder tab to carry out a brute force attack and see if the website allowed multiple attempts for the OTP. Now, to figure it out I carried out a brute force attack, for the first attempt I saw the OTP that I got and made a long list of nearly 150 number and included it at the very end to just know if the process will work out or not.
I guess I was in luck when the brute attack worked. Burp Suite was able to detect which one was the correct OTP. Moral This is one of the biggest mistakes that i have encountered in my time while carrying out pen-testing, where we never check the number of times the OTP is entered, or the number of times passwords are entered etc. Prevention method for such brute force attacks could be a check that disallows any attempt made more than 3–5 times, or the OTP should not be valid further after 5 wrong attempts or so. This kind of security technique can be implemented and it will help curb a huge number of security issues. If you enjoyed it please do clap & let’s collaborate. Get, Set, Hack!




Hii
ReplyDeleteHello
DeleteWe provide the best services, which are redefined, best-revised services. Work in Cyber Security to provide an integrated service in Cloud Computing, Web Development, Digital Solutions, and Technical Support.
ReplyDelete